Security Services
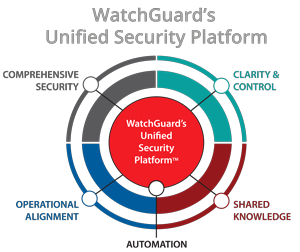
Unified Security Platform
A unified security platform integrates multiple security functions into a single, cohesive system to streamline protection, detection, and response across an organization’s digital environment. Instead of managing separate products a unified platform brings them together for streamlined visibility, control, and response. This approach eliminates silos, reduces complexity, and enhances efficiency by providing a single pane of glass for security operations. Real-time analytics and AI-driven insights enable proactive threat detection, identifying vulnerabilities before they are exploited. Automated workflows accelerate incident response, minimizing damage from breaches. Ideal for businesses of all sizes, a unified security platform helps create a more resilient and manageable cybersecurity posture in today’s increasingly complex threat landscape.

Network Security
Network security protects computer networks from unauthorized access, cyberattacks, and data breaches. It involves tools and policies that monitor, detect, and respond to cyber threats like malware, phishing, and hacking attempts. A strong network security strategy safeguards sensitive information, ensures business continuity, and maintains the integrity of connected systems. A unified security platform streamlines these processes, ensuring robust defense and compliance.
EndPoint Security
Endpoint protection with a zero-trust model secures devices by assuming no user or device is inherently trustworthy. Combining antivirus, threat detection, and strict access controls, it helps prevent breaches, isolates threats, and ensures only authenticated, authorized users and devices can interact with sensitive systems and data. Integrated into a unified platform, it ensures robust, scalable defense, minimizing risks across diverse endpoints while maintaining compliance

Wireless Security
Wireless security protects Wi-Fi networks from unauthorized access and cyber threats. It uses encryption, strong authentication, and secure configurations to prevent data breaches and eavesdropping. Effective wireless security ensures safe, reliable connectivity for users while protecting sensitive data and devices from potential attacks. Integrated into a unified security platform, it ensures robust, scalable protection for wireless environments, maintaining compliance and secure connectivity.
Identity Security
Identity security protects user identities by ensuring only authorized individuals can access systems and data. It uses tools like multi-factor authentication, single sign-on, and identity governance to verify users and control access. Integrated into a unified security platform, it ensures scalable, robust protection, maintaining data integrity and compliance while safeguarding user access across diverse systems and environments.

Remote Management
Remote management allows us to monitor, maintain, and troubleshoot systems from any location, enhancing flexibility and reducing downtime. It enables efficient updates, security patches, and support without needing physical access to devices. This approach is ideal for small to medium sized businesses that don’t have a dedicated IT support staff. This allows us to be more proactive in resolving issues instead of being reactive to when issues arise. Remote management tools offer centralized control, real-time alerts, and detailed reporting, ensuring systems remain secure and optimized.

Offsite Backup
Offsite backups provide a critical layer of protection against data loss due to hardware failure, natural disasters, theft, or cyberattacks like ransomware. They ensure business continuity with quick data recovery, minimizing downtime and financial loss. Regularly scheduled, automated offsite backups offer peace of mind, knowing your vital business information is safe and recoverable. By mitigating risks of data loss and enabling seamless restoration, offsite backups are essential for businesses prioritizing resilience, data integrity, and operational efficiency.

Email Security
Email security is vital for protecting your business from phishing, spoofing, and data breaches. Technologies like SPF, DKIM, and DMARC help verify that incoming and outgoing emails are legitimate and not forged, reducing the risk of domain impersonation. DMARC enforces policies to block fraudulent emails, SPF verifies sender domains, and DKIM adds cryptographic signatures to ensure authenticity. Educating employees to recognize phishing attempts and follow safe email practices adds a critical human layer of protection against cyber threats. Together, robust protocols and informed users create a secure email environment, safeguarding sensitive data and ensuring compliance.

Microsoft Partner
As a Microsoft reseller, we provide businesses with access to trusted Microsoft products and services, including Microsoft 365, Azure, and Windows licensing. We help our clients choose the right solutions for their needs, streamline deployment, and ensure compliance with licensing requirements. We help businesses implement Microsoft tools like Microsoft 365, Azure, and Teams with confidence, ensuring optimal performance and security.

